

Your Guide to a Robust Security Posture
This framework is essential for managing cybersecurity risk and serves as the crucial next step after understanding security controls. While controls generally fall into three categories (Preventative, Detective, and Corrective), this framework organizes them into a comprehensive structure.
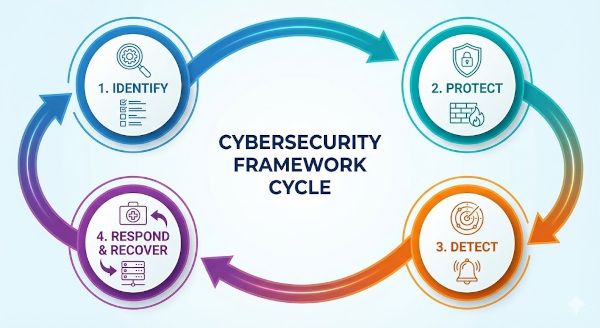
The foundational pillar. You cannot protect what you don't know you have. This phase is about gaining a clear understanding of your organizational footprint.
Implementing safeguards to ensure the delivery of critical infrastructure services. This involves putting Preventative Controls into action.
No protection is 100% foolproof. Spotting threats quickly is vital. This relies heavily on Detective Controls to identify anomalies and potential breaches.
The action plan for when an incident occurs. This phase focuses on containment, eradication, and restoration using Corrective Controls.
These four pillars form a continuous cycle, creating an adaptive and resilient cybersecurity program that evolves with the threat landscape.